I am sure many have you have read about "Hacked / Defaced with
shells", So I am pretty sure that the first thing that comes to your
mind is "What the heck are these shells?" . So this article would give
you complete idea about shells and its use.
I will soon write about "RFI, LFI" which are somewhat connected with shells. Meanwhile, keep playing with it and learn more. As without practice you won't get anything.
Difference between FTP & Shells:
Many times I see that some of us know how to use the shell but once
they have uploaded they get confused. So to start with, Let me give you
some information about FTP:
Whenever you want to open your website, the first thing you will do
is to get some web hosting for your self. That cud be either free or
paid. When your get your hosting services, you create a website on your
computer first and then upload it to your hosting server so it becomes
a World Wide Web. This process of uploading the documents from your
computer to your hosting server is done through FTP [File Transfer
Protocol]. It basically looks like a program with 2 columns, one column
shows your computer files and another shows your servers files. Just
like when you copy the stuffs from some USB drive to your computer. So
here, I will show you an example is how you would connect if you own
example.com. So when you want to connect your self to your web hosting
server, following information is required in order to authenticate
yourself:
Server : ftp.example.com
Username: XEO
Password: whatever
So, once you put in this information, server understands that you are
XEO and gives you access to all the files on the server so you can
work on it.
Since you understand the FTP now, we know that none of us will get
access to Go4expert's server because we don't have the username and
password authenticate yourself. Somehow we can manage to get the access
to G4E's FTP we can easily remove/edit/replace files. So we can destroy
this entire forum and upload our own stuffs. That is when shells comes
into the picture. Shells are a malicious PHP files which you will need
to upload to any website, and once you execute it you will get access
to its server directly
WITHOUT authenticating your self.
I wrote the difference between FTP and shells so that you guyz can
understand it, because lots of people tends to get confused between
them. So again to make it clear, you can following thing:
FTP is a protocol that lets you connect your computer to your
hosting server so that you can upload/edit/delete/replace your files.
Since we wouldn't have the username & password to connect to any
website's ftp, thats why we will use the SHELL to get access. SO SHELL IS NOT FTP BUT IT GIVES YOU ACCESS TO THE HOSTING SERVER.
Let me tell you guyz why i gave time to write this much about FTP in
this article.I remember i saw couple of threads which said following
thing:
"Hi guyz, i managed to hack my 1st website today! YAY, I am
really happy! But theres only 1 problem, i uploaded the shell and ran
it and it worked fine. The only problem is i dont have access to FTP."
Y0, i hacked a website today, uploaded a shell and it worked fine, now i am trying to get access to FTP
Shell is not a tool that you can run and complete your work. As I
said, its just a normal ".php" file, you have to find a way in any
website to upload that shell. The Idea is, you upload the shell to any
website so it will be saved on their server and it will give you the
access to it.
Phase 1 : Uploading a shell:
Suppose you want to hack "something.com". So the first thing that you
will do is, open up "something.com", and try to find some place from
where you can upload the files on the website. There are many such
places for example, "file uploads, avatars, resume upload, cooking
recipe uploads, upload your photo". So these are the places which will
give you an opportunity to upload your shell. All you have to do is, try
to upload the shell.php which is located in your computer and click on
submit. So suppose you went to the webpage
"something.com/submit_resume.php" and you uploaded your resume.
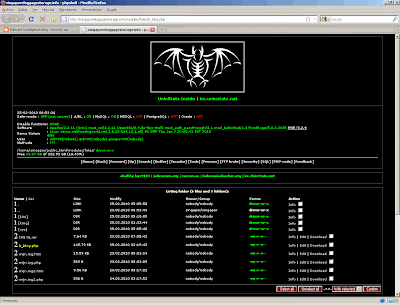
Phase 2 : Executing your uploaded shelll:
Once we have uploaded the shell as shown in "Phase:1", we know that
its sitting on the server. The only thing we need to do now is to
execute the shell from a browser so we get access to it.
So suppose i uploaded my shell as an attachment in any thread. SO now
that attachment is sitting on that thread's server. Now if we want to
executive it, we will use following URL:
Code:
http://www.something.com/forums/attachment.php?attachmentid=456&d=1249607339
So that is the DIRECT url to the attachment which is called
EXECUTION. In the same way if you execute your shell, it will take you
to a webpage where you will see everything thats on the server. And you
will have
FULL ACCESS to remove/edit/replace/delete the files. So you are another
XEO !
Phase 3 : Defacing:
Defacing is a word which means "replacing the current index file
with our own index with our motive and slogan on it". So once you have
access to the server, you are the king
- Different types of shells:
There are many shells available, most of them are public and some of
them are private. Most of them does the samething to give you the
access of the server. "c99, r57, b0yzone, j32" are some very common and
easily available shells.
- Where do I get them from?
The best way is Google search with "inurl:c99.txt". You can replace c99 with r57, j32 or anything else.
Important Piece of advice
I would suggest you to download WAMP SERVER, which lets you make
your own server on your comptuer. And then try to use shells on it.
Which will help you avoid hacking in live environment. Because, if
webmaster is smart then, he can simply check the logs for that shell
fine and track down your IP which executed the shell. Then you might be
in problem.
Thanks for your time to read the article . Hope you liked it . PEACE!